Audit your web server using Lynis
by Felix Kinaro About 2 min reading time
Lynis is a security auditing tool developed by CISOfy. It is compatible with Linux, macOS, and *NIX systems. The tool can be used to align operations to conform with data security requirements of HIPAA, ISO27001, PCI, DSS as well as system hardening.
This article assumes that you are using a Linux distro such as Ubuntu, and that you have sudo rights on the system.
Use it without having to install (You're gonna need Git)
- Install git if you do not have it already. Run sudo apt install git on terminal, or use a graphical tool. Choose your poison.

- Clone the Lynis repository to your local machine. On Terminal, type git clone https://github.com/CISOfy/lynis.git.
You can also go to _https://github.com/CISOfy/lynis_ and click the Download Zip button. Extract the contents of the zip file and open the directory. - Right click any blank area within the folder and select Open in Terminal.
- Run sudo chown -R 0:0 * to recursively set the ownership of the files to user root. Run ls -l to verify ownership

- Run sudo chmod +x lynis to make the script executable. From the above screenshot, you can see that permissions for the script are set to allow the owner to execute it (-rwxr...)
Start using Lynis
- Type sudo ./lynis audit system to audit you local Linux machine.

Use sudo ./lynis audit system remote, or connect to the server via SSH.
Replacewith the IP address of a server you own. Be warned that auditing a system you have no right to could have serious legal consequences as per your state laws.
So, what is checked when you run the above command on a local server?
- Lynis checks:
- OS in use
- GNU/Linux kernel
- System tools
- Boot loaders, startup services
- Memory and processes, whether zombie processes, active or IO waiting processes
- Users, groups and authentication.
- File systems: mount points, /tmp files, root file system
- Storage: usb-storage, firewire ohci
- Vulnerable/upgradable packages, security repository
- Software: firewalls such as iptables, webservers like Apache & nginx
- SSH support: SSH configuration
- SNMP support Databases: MySQL root password LDAP services
- PHP configuration. As of 2nd June 2019, 79% of web sites run a version of PHP.
- Tasks scheduled using crontab/cronjoband atd
- Security frameworks: AppArmor, SELinux, grsecurity status
- File integrity of installed software.
- Installed malware scanner
And many more. You can see the scan result for my personal computer below.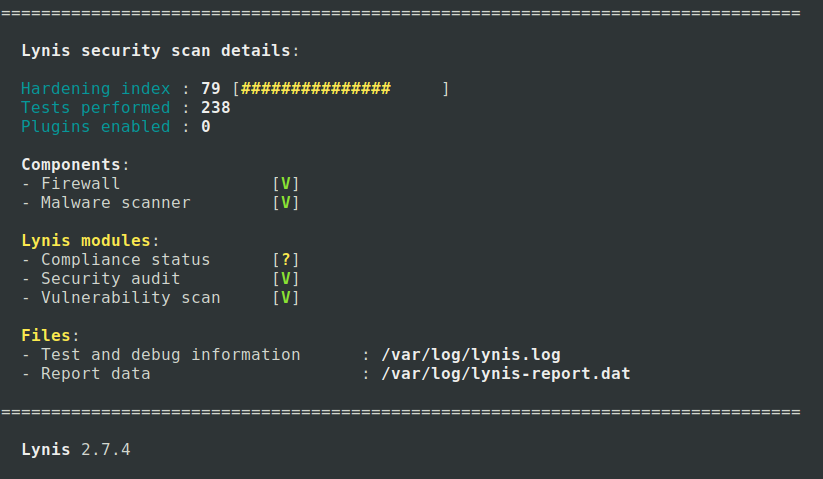
Keep in mind that prevention of compromise will eventually fail, but with the right knowledge you can stop attacks when they occur